MxM OWASP CRS Modsecurity Plugin
Traefik Modsecurity Plugin

this is a fork of the original: https://github.com/acouvreur/traefik-modsecurity-plugin
This fork introduces alpine images, CRS 4.x suppport, a custom http.transport, and a 429 jail for repeat offenders
see: https://github.com/traefik/plugindemo#troubleshooting
Traefik plugin to proxy requests to owasp/modsecurity-crs:apache


Demo
Demo with WAF intercepting relative access in query param.
Usage (docker-compose.yml)
- docker-compose up
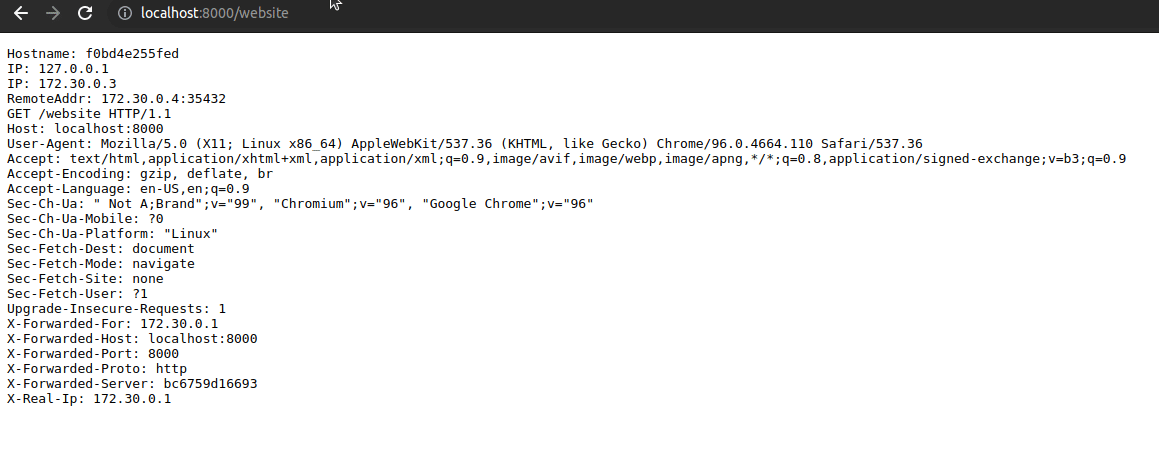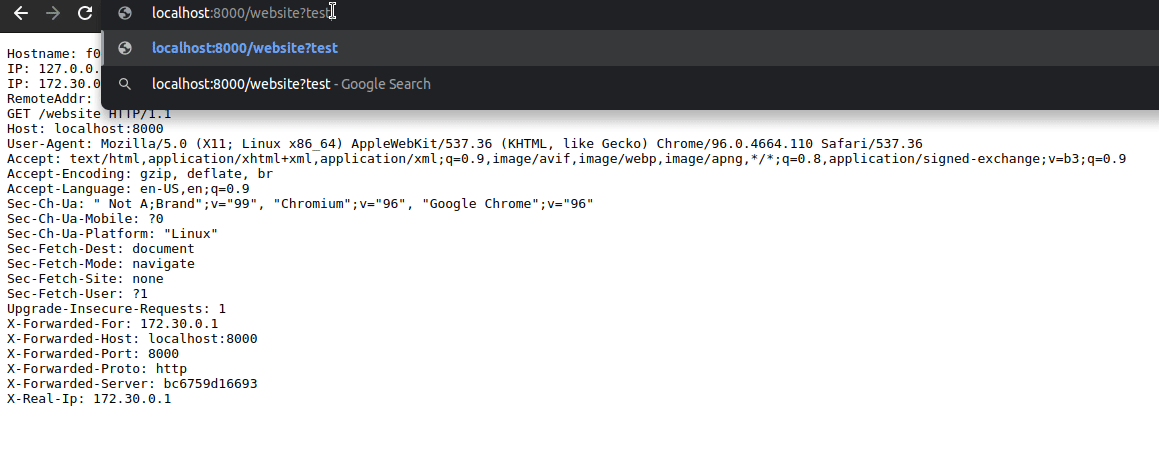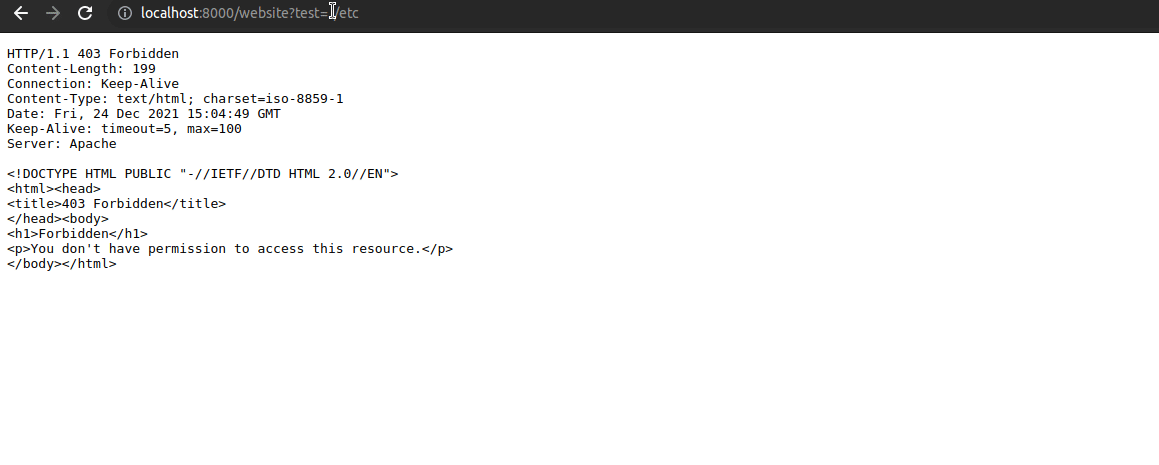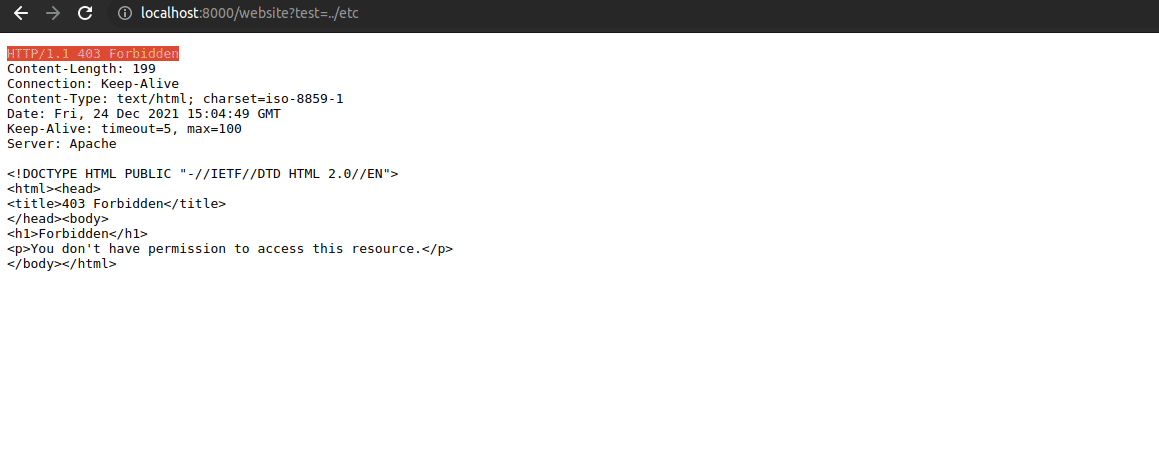
- Go to http://localhost/website, the request is received without warnings
- Go to http://localhost/website?test=../etc, the request is intercepted and returned with 403 Forbidden by owasp/modsecurity
- You can you bypass the WAF and check attacks at http://localhost/bypass?test=../etc
How it works
This is a very simple plugin that proxies the query to the owasp/modsecurity apache container.
The plugin checks that the response from the waf container hasn't an http code > 400 before forwarding the request to the real service.
If it is > 400, then the error page is returned instead.
The dummy service is created so the waf container forward the request to a service and respond with 200 OK all the time.
Configuration
This plugin supports these configuration:
modSecurityUrl: (mandatory) it's the URL for the owasp/modsecurity container.timeoutMillis: (optional) timeout in milliseconds for the http client to talk with modsecurity container. (default 2 seconds)jailEnabled: (optional) 429 jail for repeat offenders (based on threshold settings)JailTimeDurationSecs: (optional) how long a client will be jailed for, in secondsbadRequestsThresholdCount: (optional) # of 403s a clientIP can trigger from OWASP before being adding to jailbadRequestsThresholdPeriodSecs(optional) # the period, in seconds, that the threshold must meet before a client is added to the 429 jail
Local development (docker-compose.local.yml)
docker-compose -f docker-compose.local.yml up to load the local plugin
